Multi-factor authentication (MFA) has become more than just an added layer of protection for your accounts. It is essential. As phishing attacks and hackers get smarter and quicker at accessing sensitive data, it’s extremely important to add different types of layers to your password protection.
Estimated read time: 4 minutes
Multi-Factor Authentication – What is it?
MFA for short, multi-factor authentication is a security process that requires a user to present a combination of two or more different authenticators to verify their identity and access their account. The reason multi-factor authentication is important is because it increases your security. If one credential becomes compromised, unauthorized users will be unable to meet the second authentication requirement and will not be able to access your network. [1]
Some examples of MFA are PIN numbers, security token or app, email or text verification, fingerprint, facial or voice recognition, etc. We will dive more into these in the next section but knowing that there are different categories of MFA credentials is important. You want to include a minimum of one credential from two of the three categories to be considered MFA compliant.
Typically for MFA we most often see two-factor authentication where the user logs in with a username and password followed by a unique one-time code sent to their phone or email. Even though this is the standard you most often see, it is highly recommended that you enable three-factor authentication to provide the enhanced layer of protection. This is especially recommended for businesses where there are more risks of exposure to cyber criminals with the amount of sensitive information needing to be protected. [3]
The Essential Parts of MFA
It’s not enough to implement MFA. You must know how to implement it properly to maximize the security aspects and the entire reason MFA is recommended. When it comes to implementing MFA, it is recommended that you implement three different types of authentication, however, to be compliant, only two types of authentication are required.
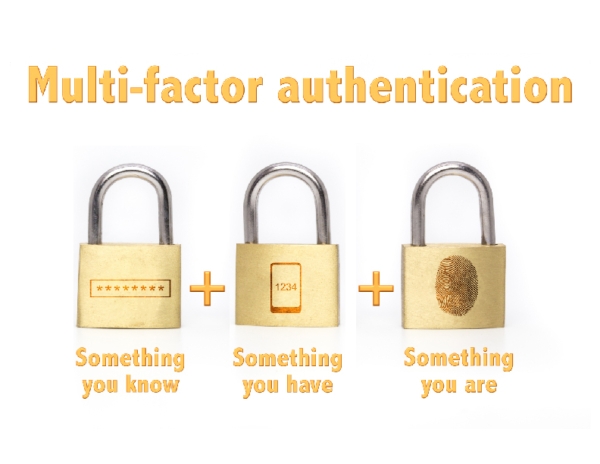
The MFA Categories [2]
1. Something you know.
This should be something like a password or PIN (Personal Identification Number). This step in the authentication process is something that you have to know. It is something that no one else can know because it isn’t a physical item. Someone might know this authentication but only if you’ve told them or if you have it written down where they can access it. This is why MFA exists. Without the other “pieces” to the password puzzle, each step on its own is useless.
2. Something you have.
This should be something physical such as a smart card, mobile token, or hardware token. This is the second layer of protection and requires the user to physically have it in order to access the system. Without it, there can be no access.
3. Something you are.
This final piece to MFA is some form of biometric factor such as facial recognition, fingerprint or voice recognition. Because this is a physical part of your body, it adds that final layer of protection making it impossible for someone to access the secure system without it.
By enabling three-factor authentication, if one or even two of the MFA factors are compromised, the data is still secure as the unauthorized user is not able to get past all three authentication pieces.
When should MFA be added?
How do you know when MFA should be implemented? MFA is highly recommended for internet-facing systems such as email, remote desktop and Virtual Private Network (VPNs). You should always consider matching the capability to the need when it comes to security solutions. Some applications are secured just fine with only two-factors and others are highly sensitive and need the triple layer of protection. Evaluate your needs and choose a solution that best fits. When in doubt, having three layers is always best.
MFA Evaluation and Recommendations for Businesses
Because the cybersecurity environment is ever-changing, it can be tough to stay on top of the new hacker trends and how MFA recommendations change over time. There are resources available online as well as organizations that focus on these topics. Again, that can be a lot to take in and can be very time consuming to research. We recommend that you work with an expert in the field and have them evaluate your security needs on a regular basis. They are equipped with the latest information and have the knowledge to quickly adapt to the ever-changing environment.
At Hamilton, we have a team dedicated to cybersecurity solutions and over 20 years’ experience in the industry. Working with a team such as ours gives you peace of mind that you are covered. In addition, should the need arise, you have a team to quickly handle any compromised access situations.
Our team offers free consultations where you can speak with our experts and ask them questions specific to your needs. We can test and provide an evaluation of your current security status while offering recommendations and next steps for changes. Knowing your baseline is essential. This first step is often overlooked; however, it is an important one. If you are looking to have someone evaluate your current business security, our team would be happy to help you. Please fill out the form below and we will reach out to you!
Did you know that cybersecurity isn’t something you can just pick up off the shelf and buy? You would be surprised at what all goes into the world of cybersecurity. Find out more here: “Alert: Cybersecurity is a Process, not a Product”.
Ready to take the next step in protecting your business?
________________________________________________________







