Don’t worry, you won’t need to pull an all-nighter to prepare for a cybersecurity risk assessment for your organization. In fact, the only work you’ll need to do is locate a trusted provider to perform the review and analysis needed to help protect you from costly security incidents and compliance violations.
Estimated read time: 3 minutes
What is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is an evaluation of your business network and systems to identify areas within the business or organization that are most vulnerable to cyber threats. Vulnerabilities can be found in a business anywhere from individual PCs to entire networks, and even within the actions and training of your team. With cyberattacks increasingly on the rise, every business is susceptible and needs to take actions now to patch vulnerabilities and train their staff.
A cybersecurity risk assessment will give you an idea of what your company’s security posture looks like. A trusted provider will identify and rank areas that are the most vulnerable and need to be reviewed, giving serious consideration to those components that are most critical to your business.
At a high level, a thorough assessment will include:
- Testing your security controls.
- Evaluating your security posture and understanding the baseline cybersecurity measures you already have in place.
- Identify vulnerabilities and areas needing attention.
- Demonstrate preventative measures that can be put in place to prevent network and data breaches.
The most common place to start with a risk assessment is with a Network Penetration Test followed by a Vulnerability Assessment. Both tests provide valuable information for identifying different areas of concern.
Network Penetration Test:
Network penetration testing (pen-testing) intentionally simulates the tactics cyber criminals would use to gain access to your network and data. By simulating these tactics, the penetration tester will identify security vulnerabilities in networks, systems, and devices. Once these vulnerabilities are known they can be remediated to better protect your network.
Vulnerability Assessments:
Vulnerability Assessments are the second layer in identifying vulnerabilities in your system. Rather than scanning for the purpose of breaching your network, this assessment process seeks to identify weak spots, so you know where to place your focus in prevention. Once these are identified, a comprehensive plan can be developed to ensure those areas of weakness are addressed providing security in the future.
Making the Grade
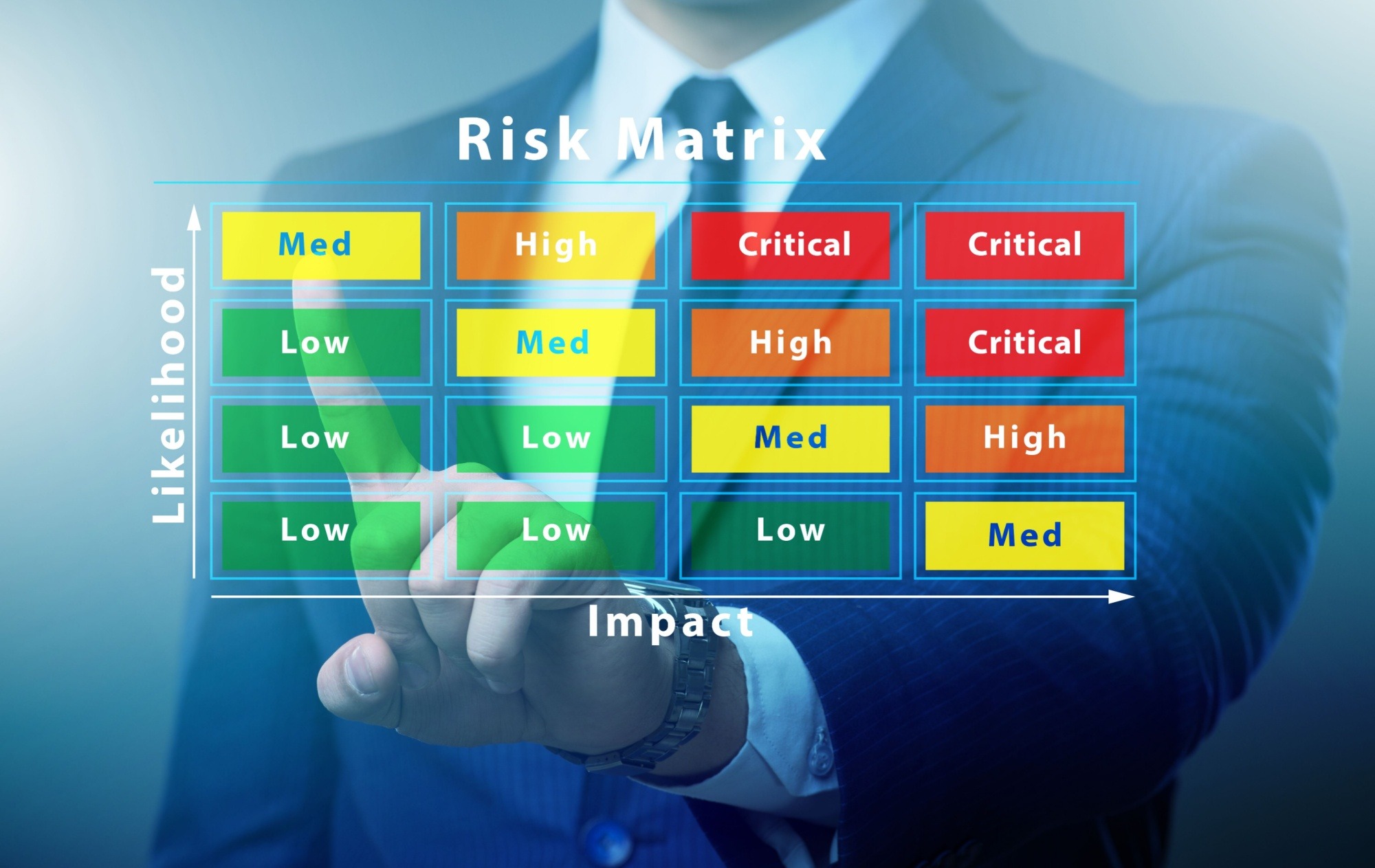
Once the initial steps of the Cybersecurity Risk Assessment are completed and assets have been evaluated for vulnerabilities, a written report of the identified risks and preventative actions needed to correct and prevent further incidents is provided. As risks are assessed, they are evaluated to determine the level of risk (critical, high, medium and low). A risk matrix helps illustrate that not all threats are created equal. The level of the potential threat is determined by the threat’s ability to be discovered, exploited, and reproduced along with the amount of harm the threat can cause to the organization.
Follow the Plan
It’s not enough to only assess and have a remediation plan in place. It’s equally important to follow the plan AND have the plan reviewed periodically with a third-party expert. Vulnerabilities and risks are changing on a daily, even hourly basis. As such, you need a plan and protection in place that can adapt to the changing threats. Hamilton has expert tools that work behind the scenes to ward off these threats — all while you continue your regular day-to-day activities. Knowing that someone is reviewing, remediating and preventing cyberattacks is peace of mind that everyone operating a business can appreciate. Hamilton focuses on the protection, so you can focus on growing your business.
Now is the Time to Put Your Cybersecurity Plan in Place
It’s time to take action and have a Cybersecurity Risk Assessment completed for your organization. Working with an expert such as Hamilton gives you the peace of mind that a thorough review has been completed and you know what action to take next to mitigate your risks. As cyber threats change daily, the process of identifying potential vulnerabilities is ongoing. Hamilton has regular reviews and plans in place to stay ahead of these vulnerabilities so you don’t have to. Contact our team at 308-381-1000 or email us below and we will connect with you to work together to protect your business.
Not sure if your business needs a Cybersecurity Risk Assessment? Find out here “Does Your Business Need a Cybersecurity Risk Assessment — Interview”.
Let us complete a Cybersecurity Risk Assessment for your business.
Fill out the form below and one of our expert team members will be in contact with you very soon!
Feel free to call us directly at 308-381-1000.
Discover more about Hamilton Business Solutions here!






