Without even knowing it, your business is constantly exposed to a variety of digital risks. Protect your business by assessing and remediating your network vulnerabilities. You can be prepared. Read on to learn about two important network assessments the experts recommend.

Without even knowing it, your business is exposed to a variety of digital risks. These risks happen multiple times per day and possibly multiple times per hour. Through expert network assessments, you can be prepared to assess and remediate any potential network risks.
Bring in the Experts
Working with an expert in the cybersecurity industry is an important first step. A third-party expert can bring in the tools and experience to test for vulnerabilities in your network and ensure you have the pathway and solutions to remediate them. While many companies claim to be experts in cybersecurity, there are a few important things you should consider when hiring an expert.
- How long have they been in business?
- Are they aware of all the regulatory restrictions around cybersecurity?
- Are they available 24×7 for support and service should a need to mitigate a vulnerability arise?
- Do they offer a customized service that meets your company’s specific needs?
Two ways that a trusted cybersecurity partner can evaluate your network are Network Penetration Testing, also known as Pen-Testing, and Vulnerability Assessments. Each will find vulnerabilities and is a valuable step to ensure your network, devices and business stays secure.
Part 1: Network Penetration Testing
Network penetration testing (pen-testing) is one of the first steps you can implement in your business to identify potential security vulnerabilities in your networks, systems, and devices. Through pen-testing, simulated attacks are pushed to your network. These simulations are used to evaluate weaknesses at the edge of your network that could potentially provide an opening for cyberattacks.
Part 2: Internal Network Vulnerability Assessment
Putting your system through a simulated attack will give you one picture. However, in order to get a holistic picture, an Internal Vulnerability Assessment will take a different snapshot. Rather than scanning for weaknesses on the outside of your network, the vulnerability test works from inside your network. Simulating the scenario of what an attacker would see gives insight into the data that could be breached by an attacker in your system and ultimately identifies your biggest security concerns.
Through both pen-testing and vulnerability assessments, you can gain a more comprehensive picture of your network and data vulnerabilities which allows you to analyze and remediate your risk. You should always be assessing the vulnerability of your system and be putting measures in place to stop any potential hackers from gaining access. Through vast experience and a long history of providing network security, Hamilton has developed a 4-step-process for analysis, remediation and protection of your business network and systems.
This network vulnerability assessment allows them to get a comprehensive look at your network and provides them the intel into possible weak network spots so they can determine the best course of action for mitigating and ultimately preventing the potential security risks found.
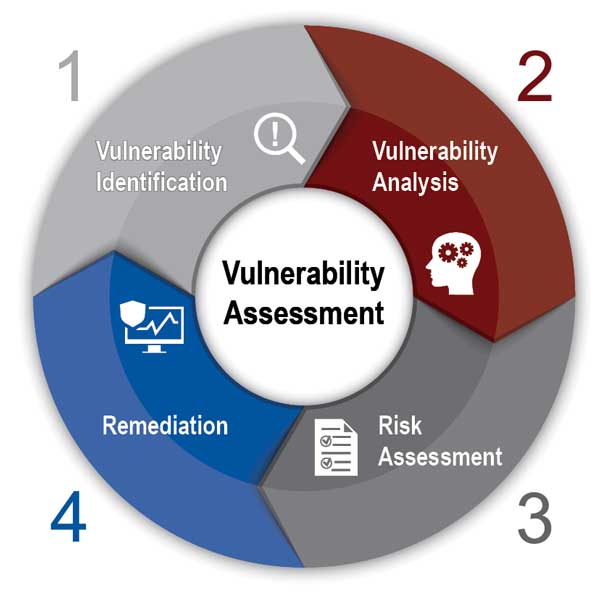
Part 3: Identify, Analyze, Assess and Remediate
Vulnerability Identification
This network assessment, comprised of the pen-test and internal vulnerability assessment, provides data regarding potential weaknesses in the network. Learn if your hardware is harming your network.
Report Analysis
A comprehensive report is delivered, defining the vulnerabilities identified during the pen-test and vulnerability assessment and, the root cause of each threat. This step is critical to understand the exact vulnerabilities and provide recommendation for remediation or mitigation.
Risk Assessment
Through the analysis, each vulnerability that is discovered is assigned a severity level. Knowing the critical, high, medium and low risk items allows for prioritization and remediation.
Remediation
Hamilton experts then begin implementing measures to remediate and mitigate the discovered vulnerabilities. A complete record and report of your vulnerabilities ensures you have a baseline for future efforts and to ease your ongoing cybersecurity efforts.
Are you ready to have your system tested by an expert in the industry? Schedule a free consultation with our team and learn more about incorporating network vulnerability assessments into your business ASAP.





